Corporate concerns about entrusting sensitive data to third-party platforms keep many CTOs awake at night. Every time data leaves your infrastructure for a bolted-on BI tool, you're gambling with control. The stakes? Regulatory compliance, competitive advantage, and customer trust.
Deploying a business analytics solution while keeping data safe and compliant often involves choosing between BI solutions that are either “bolted-on” or “embedded”. Bolted-on solutions are external to the core data system, while an embedded solution is just that: an integrated part of the original design.
Here's the reality: embedded analytics hosted on-premises or within your VPC isn't just safer; it's the only viable path for handling sensitive PII, HIPAA-protected records, or financial data. Security becomes your foundation, not something you retrofit later.
The Data Sovereignty Problem With Bolted-On BI
Traditional BI tools mandate external transmission. Your data travels outside your perimeter, creating copies on third-party infrastructure. This movement violates GDPR residency requirements and HIPAA safeguards before you've processed a single report.
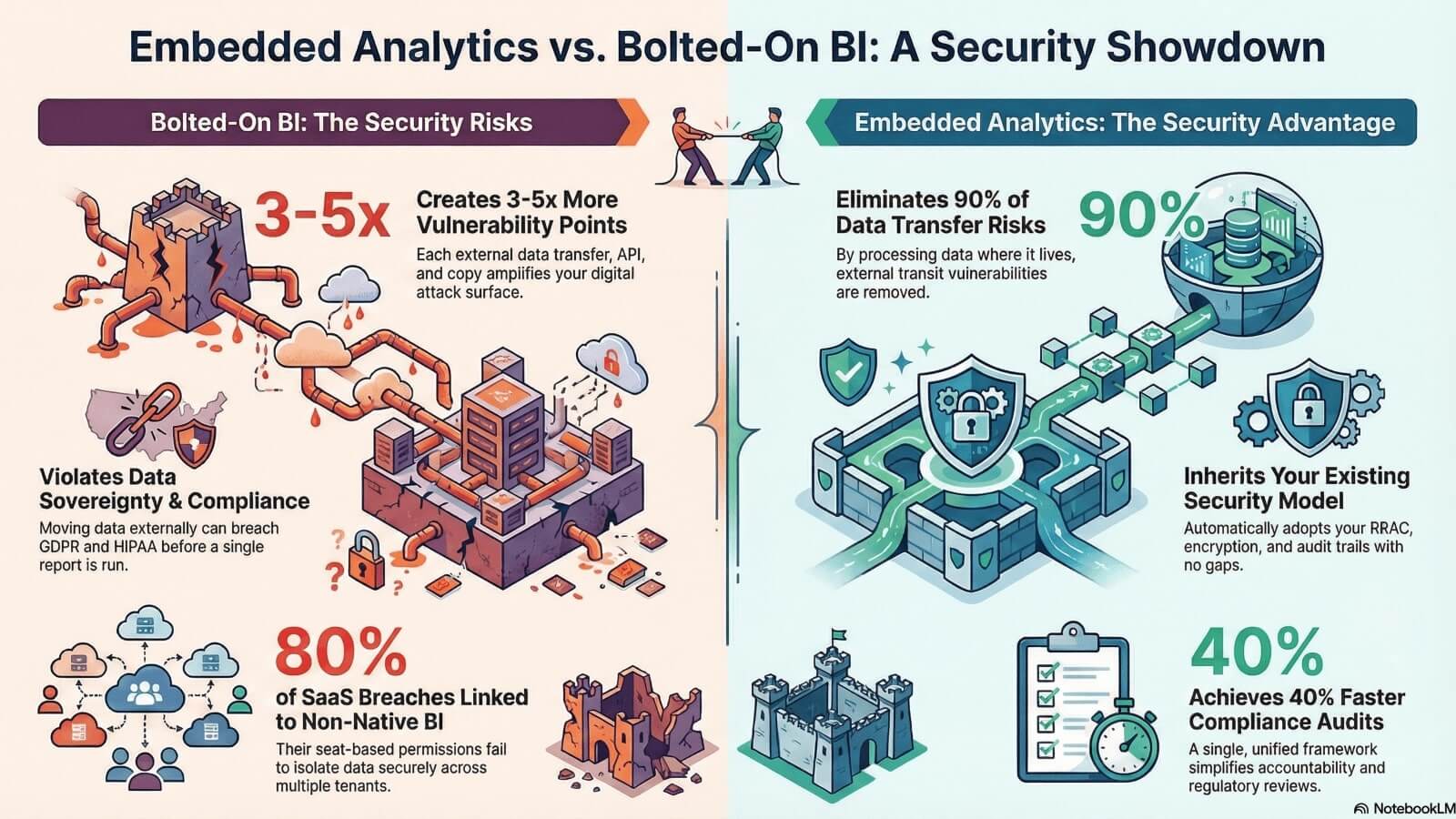
Bolted-on solutions create 3-5x more vulnerability points than embedded on-premises processing. Each API endpoint, each transit hop, each external copy amplifies your breach surface. Your security team didn't design these pathways. The vendor did.
Embedded analytics should be treated as a privileged participant. It runs in your application, affects sensitive data, and is exposed to your users, which means it must be governed like any other critical supplier.
The Retention Trap Nobody Discusses
Third-party BI platforms retain copies of your data indefinitely. Read that again. When you need to honor a deletion request under GDPR's "right to be forgotten," you're at the vendor's mercy. Their backup cycles, their retention policies, their compliance timelines, not yours.
Embedded analytics keeps processing within your firewall. No data residency risks. No vendor lock-in. Your data governance framework, i.e. the rules, processes, and responsibilities that regulate how your organization manages data, stays intact without manual syncing or policy drift between systems.

Architecture That Eliminates Risk
The structural differences between embedded and bolted-on BI determine everything about security outcomes.
Attack Surface Reduction
Embedded analytics processes your original data where it already exists. Rejecting the use of an external dashboarding tool means preventing unmanaged data transit and breaking the custody chain. You eliminate up to 90% of external data transfer risks immediately.
Those aren't just endpoints you're closing; They're persistent vulnerabilities that create an ongoing and very real threat of exposure and failure of compliance. Every connection point bolted-on BI requires represents another opportunity for interception, misconfiguration, or breach.
Security Model Inheritance
On-premises embedded solutions automatically adopt your existing role-based access control (RBAC) protocols, encryption standards, and audit trails. Nothing new to sync. No conflict between maintaining a strong security posture and maximizing your analytical capabilities.
Bolted-on BI forces manual mapping. Your team spends time translating your security model to fit into the vendor's framework. Gaps emerge. Updates lag. The disconnect grows over time, creating blind spots in your security coverage.
This isn't just inconvenient; it increases the compliance burden. Conversely, when auditors review your systems, embedded analytics extends your existing frameworks seamlessly. No third-party audits required.
The Multi-Tenancy Security Crisis
SaaS providers face unique pressure. Traditional BI tools weren't built for multi-tenant embedding. They were designed for internal seats, not secure isolation at scale.
Eighty percent of SaaS multi-tenancy breaches stem from non-native BI embedding. The math is brutal: bolt-on solutions leak data across users when tenant isolation breaks down under load.
Row-Level Security Enforcement
Seat-based access models don't translate to multi-tenant requirements. Your SaaS app might serve thousands of external users. Bolted-on BI often applies coarse permissions that can't handle the granularity you need.
Embedded platforms deliver row-level security within your application context. Users see only the data they're authorized to access, enforced at the appropriate levels through your existing security logic. No translation. No gaps.
Real-World Impact: Case Studies
Healthcare SaaS Recovery
A healthcare SaaS provider discovered HIPAA violations from their bolted-on BI's external data pulls in a multi-tenant setup. Patient records crossed organizational boundaries through inadequate isolation.
The switch to self-hosted embedded analytics brought data back on-premises. RBAC inheritance worked immediately. Results: zero breaches post-migration, 40% faster compliance audits, and tenant isolation that held through 10x user growth.
Financial Services Avoids Disaster
One financial firm tried embedding traditional BI into client portals. Multi-tenancy flaws exposed PII across customers through inadequate RLS, or Row-Level Security.
Regulatory review uncovered the problem before a formal breach occurred - barely.
Migration to on-premises embedded cut their attack surface by 70%. Full data sovereignty returned. They avoided a $2M GDPR fine and retained their customer base through transparent communication about the fix.
Performance Without Compromise
External BI introduces latency from data movement. Teams feel pressure to take shortcuts - cached data, less frequent updates, simplified queries. Each "optimization" erodes security.
Embedded solutions use in-memory on-premises processing. No compromises. You get speed and sovereignty together. Bolt-on BI asks you to choose between performance and control. That's a false choice you shouldn't accept.
The API Exposure Problem
Every API endpoint your bolted-on BI opens for data extraction represents a door. Even with encryption in transit, the architectural requirement for these connections creates persistent risk.
Embedded analytics processes metadata only. Raw sensitive data never travels externally. The difference matters when you're building defense in depth.
Transit encryption protects data in motion. It doesn't protect against misconfigured endpoints, compromised tokens, or insider threats with legitimate access. Embedded analytics removes these attack vectors from consideration.

Compliance Complexity Multiplier
External BI demands vendor-specific GDPR and HIPAA mappings. You're maintaining two compliance frameworks: yours and theirs. Audit costs increase. Reconciliation becomes a project unto itself.
Data retention mismatches across jurisdictions create additional complications. Your retention policies don't align with vendor practices. Cross-border data movement triggers additional regulations you wouldn't face with on-premises hosting.
On-premises embedded analytics extends your internal compliance framework seamlessly. One audit, one framework, one responsibility chain. Clean lines of accountability.
Future-Proofing Through Low-Code Integration
Gartner has predicted that by 2026, at least 70 percent of all new enterprise applications will be built with low-code or no-code platforms, up from around 25%. This shift amplifies the governance gap. Bolt-on BI creates blind spots in user-facing analytics that low-code developers can't easily close.
Embedded analytics ensures privacy from the architecture layer up. It's not an add-on feature you bolt on after deployment. Governance lives in the foundation of your low-code applications, preventing the retrofits that plague bolt-on approaches.
External data processing raises compliance costs by 50% due to vendor audits and retention mismatches. On-premises embedded analytics streamlines this by keeping data within your established audit framework.
The Strategic Decision
The choice between bolted-on and embedded analytics stopped being about features years ago. It's a fundamental security architecture decision.
For firms managing sensitive data, the risk of data movement is unacceptable. Embedded analytics brings insights to your data rather than moving data to your insights. This approach preserves your control over how and where it’s used, reduces the potential attack surfaces, and maintains regulatory compliance at scale.
Your security team designed your infrastructure for a reason (even if that security team is just you). Embedded analytics respect that design. Bolted-on BI asks you to compromise it.

Frequently Asked Questions
How does embedded analytics inherit my on-premises security without data movement?
Embedded tools live within your application environment. They use your existing authentication systems like LDAP or OAuth to control data access at the source. No additional layers means no potential gaps.
Why does bolted-on BI fail multi-tenant security in SaaS apps?
Traditional BI tools use seat-based permissions that don't map to thousands of external users. Row-level security fails when the vendor's model can't express your tenant isolation requirements.
Is on-premises hosting viable for real-time analytics performance?
Absolutely. In-memory processing on-premises from embedded BI generally outperforms cloud-based BI by eliminating transit latency. You're not waiting for round trips to external services.
What are the primary API risks of third-party BI?
Every external API creates potential failure and attack points. Bolted-on BI requires open ports and authentication tokens to extract raw data. These "transit vulnerabilities" don't exist in natively embedded on-premises models.
Evaluate your current BI stack honestly. If sensitive data leaves your perimeter for dashboard access, migration to embedded on-premises architecture isn't optional—it's overdue. The question isn't whether you can afford the transition. It's whether you can afford the breach that's coming if you don't.